Top Android Settings To Ensure Your Cell Phone Is Secure
Are you sure your Android cell phone is as secure as possible? Explore the top Android settings that ensure your cell phone is safe while in use.
Protect your digital foot print and personal data. Find the tips, tricks, and tools to keep your systems and information secure.

Are you sure your Android cell phone is as secure as possible? Explore the top Android settings that ensure your cell phone is safe while in use.

Cybercrime is a growing problem for businesses across the tech sector. We’ll explore some of the solutions companies use to keep their assets safe.

As the business world becomes more digitally driven, companies face constant privacy threats. This is backed by research, which reveals that over 70% of enterprises have experienced some fraud. However, some businesses are more prone to digital identity fraud than others for several reasons, including varying vulnerabilities. Cybercriminals are constantly on the lookout for such…

With everyone always connected via the internet, security and privacy are now top priorities. Here’s where VPNs come into play. For those on the go, a reliable VPN app for your iOS or Android device is essential. A perfect example to explore is https://7vpn.com/, a service that promises secure and private browsing on your mobile…

Cyber threats aren’t something to ignore. Discover some overlooked cybersecurity vulnerabilities to know about and learn how to address them.

Generative AI security risks are gripping users and experts alike. Learn more about these security threats and how to safeguard yourself against them.

Be careful when using public charging stations for your phone.

Get the latest cybersecurity certifications and start on a new career.
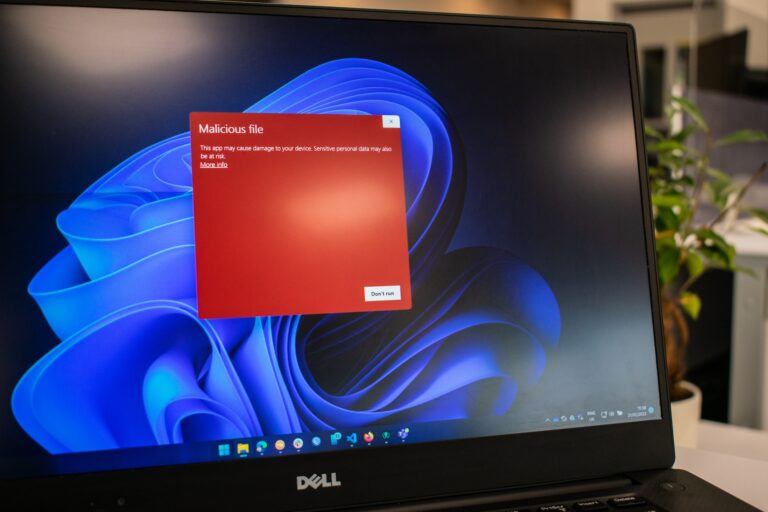
Here is what you need to know about antivirus software and potential threats.

Many people think that USB Type-C is just another design. The USB Type C flash drive with a revolutionary design has the cable and connector as one size, making it simple to locate the proper connection on your device. Besides syncing, you can also use a USB Type-C as a power supply – your device’s…

Today, analytics and data play a critical role in a company’s success. Investors, companies, and individuals working in a business setting interact with data in some form or another. The data is essential for company forecasting and consumer behaviour analysis. Companies retain vast data about their customers, especially in the healthcare sector. As a result,…

Learn how to organize your digital files, secure them in the cloud or a hard drive, and make sure they are in a spot where you’ll be able to find them later.


VPNs are important in an era of increasing digital use.