Who’s Been Using Your Mac Behind Your Back? Find Out!

Chances are, someone else is using your MacBook without your permission. This has been a major concern, especially among the people who leave their MacBook at home or work. So, if you just realized that this is happening to you, relax-you're not alone.
It is a serious privacy invasion when anyone secretly accesses your MacBook. Such an invasion is also high risk, especially if the intruder is doing it for the wrong reasons.
Dusting the entire laptop is recommended, especially if you suspect anything criminal. It would provide some clues on who put their hands on the Macbook. However, if you don't have the gear for dusting, you can take advantage of a wide variety of digital detective tools and a few commands stipulated below.
Check Login Records
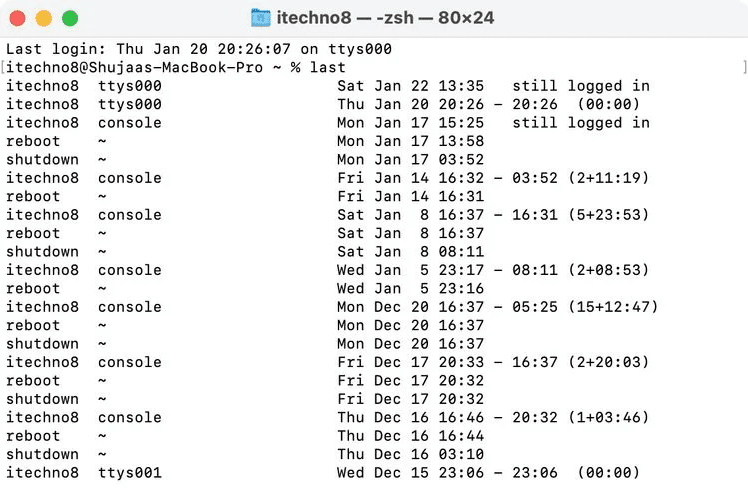
Checking your login history in Terminal would be the quickest way to check your MacBook's login history. It shows a descending record of all the events on your device. Here's how to use the “last” command.
- Open up “Terminal” on your Mac.
- Type “last.”
- Hit “Enter.”
The next window should show a comprehensive list of all the login events and the exact login time. You can check the last time your MacBook was used and guess whether someone may have secretly logged in.
Check Your System Logs
Your MacBook keeps a record of everything it does. Type the command below to access the system logs.
“log show –style syslog | fgrep “[powerd:sleepWake]”
This is a long list of system events that you might struggle to filter. But you can focus on the timestamp on each log to figure out the exact time the intruder opened your MacBook.

The logs are just entries and won't tell you who accessed your MacBook or what they wanted. However, it will help you ascertain that someone accessed your MacBook, and it's not an issue of pets pressing the keyboard.
Visit Recent Activities
Your MacBook has a record of recently opened documents and applications. The feature provides quick access when you want to re-open the docs and apps. So, you can always find out what application or document an intruder accessed on your Mac.
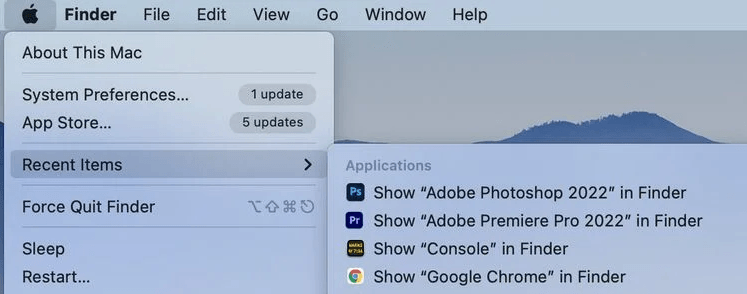
To access the recent documents/applications:
- Click the Apple Logo at the top.
- Hover mouse over “Recent Items.”
- Click on each item to see more details.
Alternatively, you can access the recent items through “Finder.” Here's how.
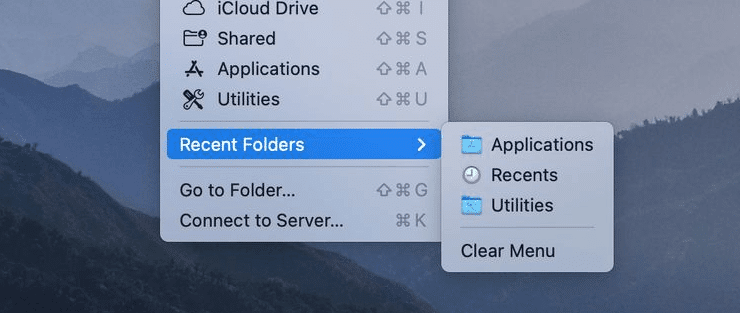
- Open “Finder.”
- Click “Go.”
- Select “Recent Folders.”
You should see a list of all the recently opened movies, documents, pictures, etc. The only limit to this tracking method is that the intruder may clear the recent items list.
Seeing a strange files on your recent items list is a piece of evidence that someone else is accessing your machine. Other programs in your MacBook also have their “History” and “Recent items” section that you can check. The web browser has a history section detailing all the recent activities. Applications like InDesign and Microsoft Word also have a separate list of “Recent Activities” that you can check to gather more evidence.
Use third-party Software
If the methods are not yielding desirable results, you could install snooping software to track the suspect. The software lets you monitor your MacBook usage remotely. The monitoring includes taking screenshots to see the activities on your machine in real-time. You can use your MacBook's webcam to see the intruder's face or take a photo.
Enhance Passwords Protection
Locking your Mac with a password is perhaps the simplest method to prevent others from using it behind your back. If your Mac is not password protected, you may want to activate that immediately. Having a password is the most effective means of warding off intruders. If you already have a password, you need to change it and not share it with anyone. You should guess who's using your MacBook going by your environment. The steps provided here will also help you rule out most major suspects.
